Identity theft protection
no matter where you are in life
Identity theft protection
no matter where you are in life
Digital identity theft is increasing.
Social networks have empowered us to share more of our passions and accomplishments than ever before, but they’ve also made personal information, such as birth dates and maiden names, more accessible to identity thieves. Complete ID’s Dark Web Surveillance can help detect when online content has put your identity at risk.
Your financial independence can be impacted by identity theft
The consequences of identity theft can have a ripple effect in multiple areas of your life. To help negate identity theft side-effects like these, Complete ID offers up to a million dollars toward the expenses of restoration.2
Identity protection made for all members of the family
Protecting you and your family from identity theft can be a tough job, especially when the effects of identity theft aren’t exclusive to adults. That’s why Complete ID offers additional Child Identity Monitoring3 so you can be rest assured that your whole family is covered.
Helps find stolen information before it can be used to cause financial damage
Stolen records can lead to unforeseen consequences for victims such as false legal charges, lost medical reimbursement, and even job loss. Complete ID monitors the dark web to help find stolen information before it can be used to cause financial damage.
How common is identity theft?
40 million U.S. adult victims experienced identity fraud in some form in 2022.
Helping secure your financial future by protecting your identity
Identity fraud losses totaled $43 billion in 2022.
Credit monitoring by itself is not enough
Credit monitoring can be a good start when protecting your identity, but you should be doing more.
Identity protection involves more than your credit report
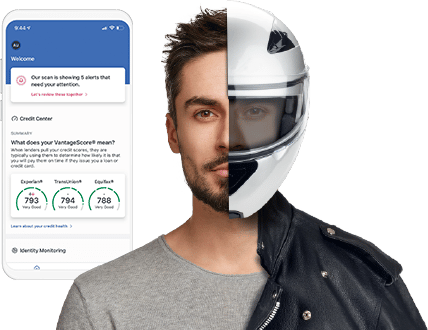
Identity protection involves more than your credit report
Credit Monitoring is Only Partial Protection
When the Rubber Meets the Road
Have you wondered what a free credit monitoring service can do to keep your identity safe? Chances are it’s not enough. Most free credit monitoring services leave it up to you to patrol your credit report and fail to detect certain types of identity theft. With credit monitoring services, there’s no one there to help put the pieces back together if your identity is stolen. Complete ID goes beyond credit monitoring by being proactive in recognizing identity threats and connecting you with our Identity Restoration Specialists if your identity is stolen.
Complete ID Can Help You
Recover From ID Theft
No one expects their information to be stolen, and when identity theft happens it can have deep financial and emotional impact. But you don’t have to face the fallout of identity theft alone. Complete ID helps you tackle the process of protecting your assets and restoring your identity.
Our Identity Restoration Specialists are standing by to help you.
24/7 Access to Our U.S. Based Support
Identity thieves don’t just work 9 to 5, and neither do we! Our U.S. based support team is here to help at any time.
What Can Our Restoration Specialists Do For You?
Once you open a case with one of our specialists, they work with you across the entire restoration process. You won’t have to waste time calling multiple departments or following complicated phone trees. Instead, you receive the direct number for your assigned restoration specialist who manages your restoration process and makes the calls for you, or along with you.
Up to $1,000,000 of Identity Theft Insurance2

Social media has a wonderful ability to rekindle lost connections with the people who are dear to us, but those connections also can leave us vulnerable to threats.
- Lost wages or income
- Attorney and legal fees
- Expenses for refiling loans, grants, and other lines of credit
- Costs of childcare and/or elderly care

More than 70 million consumers globally were impacted by a data breach.4
- Dark Web Surveillance
- SSN Identity Monitoring
- Financial Account Takeover Alerts
- Criminal Record Monitoring
- Lost Wallet Replacement
- 24/7 Member Service Support
- Annual Credit Report and Monitoring5
- Monthly VantageScore Credit Update6
- Neighborhood Watch Monitoring
- Alternative Loan Monitoring
- Neighborhood Watch Monitoring
- Full Service Identity Restoration
- Experian CreditLock7
- Digital Privacy
Password Manager, Safe Browser, Secure VPN
(Virtual Private Network)
*All plan pricing is subject to applicable sales tax. Service provided by Experian®.
2The Identity Theft Insurance is underwritten and administered by American Bankers Insurance Company of Florida, an Assurant company under group or blanket policy(ies). The description herein is a summary and intended for informational purposes only and does not include all terms, conditions and exclusions of the policies described. Please refer to the actual policies for terms, conditions, and exclusions of coverage. Coverage may not be available in all jurisdictions. Review the Summary of Benefits.
3Child monitoring includes up to 5 children under the age of 18. One-time Parent/Legal Guardian verification is required to receive alert details for children.
4Experian 2024 Data Breach Industry Forecast
5Monitoring with Experian begins within 48 hours of enrollment in Complete ID. Monitoring with Equifax and TransUnion takes approximately 4 days to begin. You may cancel your membership in Complete ID any time online or by calling 1-855-591-0202.
6Calculated on the VantageScore 3.0 model. Your VantageScore 3.0 from Experian indicates your credit risk level and is not used by all lenders; your lender may use a score that’s different from your VantageScore 3.0. Click here to learn more about this.
7Experian CreditLock™ is a separate service from Security Freeze and is an included feature in all Complete ID membership plans. This feature controls access to your Experian credit file and will not apply to your TransUnion or Equifax credit files. To learn more about Experian CreditLock and view the differences between a Security Freeze, Experian CreditLock, and Fraud Alerts please visit www.completeid.com/frequently-asked-questions.
