Know the risks
Identity theft happens when criminals get a hold of your sensitive personal information to take out loans, open fraudulent accounts, falsify tax returns, purchase properties, and use your good name to break the law.
1: How your information is taken
More than 70 million consumers globally were impacted by a data breach in 2023.1
While hacking makes up 91% of data attacks, not all threats to information happen online. Physical documents, institutional records, and lost wallets can also be used to expose sensitive information and commit identity theft. Criminals have many ways to access personal information, and some of them are completely out of your control.
…No matter how careful you are, your information can be stolen
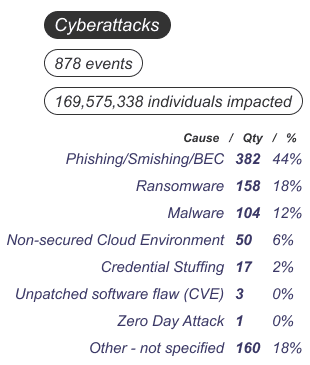
| Cause | Qty | % |
|---|---|---|
| Phishing/Smishing/BEC | 382 | 44% |
| Ransomware | 158 | 18% |
| Malware | 104 | 12% |
| Non-secured Cloud Environment | 50 | 6% |
| Credential Stuffing | 17 | 2% |
| Unpatched software flaw (CVE) | 3 | 0% |
| Zero Day Attack | 1 | 0% |
| Other - not specified | 160 | 18% |
2: What information is stolen
Identity thieves are the new pickpockets, but what they steal is more personal and damaging than cash or personal items.
Some of the most targeted pieces of information, such as full names and Social Security numbers, don’t change often over the course of a lifetime. When stolen and used by an identity thief, these more permanent pieces of information can’t be easily changed to resolve the problem.

| Name | Email Address | Social Security Number | Address | Password | Miscellaneous | Undisclosed | Credit Card Numbers | Financial | Date of Birth | Phone Number | Medical |
|---|---|---|---|---|---|---|---|---|---|---|---|
| 44.2% | 27.8% | 27.0% | 25.9% | 23.5% | 21.0% | 18.2% | 17.2% | 15.6% | 15.0% | 11.2% | 11.1% |
2: What information is stolen
Identity thieves are the new pickpockets, but what they steal
is more personal and damaging than cash or personal items.
Some of the most targeted pieces of information, such as full
names and Social Security numbers, don’t change often over the
course of a lifetime. When stolen and used by an identity thief,
these more permanent pieces of information can’t be easily
changed to resolve the problem.
3: What can happen with the information that has been stolen
Beyond the financial impact
IDENTITY THEFT CAN AFFECT YOUR QUALITY OF LIFE

Unlike other types of theft, identity theft hurts more than just your bank account.
Identity theft can affect your life options and basic necessities. When your identity has been compromised it can lead to false criminal charges, bank account charges, and a lowered VantageScore®5 Credit Score. It can eventually result in job loss, reduced access to housing, and the inability to attain credit cards, student loans, personal loans, and/or mortgages.
The consequences can extend much deeper.
How Complete ID Works
Identity Protection
There’s a lot of variety and complexity possible for every identity theft case. Simple protective measures, like annually checking credit reports, no longer cut it. It’s necessary to have a comprehensive and proactive approach to identity protection.
Credit Monitoring
It’s important to know about your financial health, just like it’s important to know about your physical health. Your credit gets a regular checkup as part of your Complete ID membership.
Restoration
Don’t get lost in the labyrinth of processes required to resolve ID theft. Our specialists know all the routes and pitfalls no matter the type of theft, so you can have years of expertise at your back when tackling your case.
*All plan pricing is subject to applicable sales tax. Service provided by Experian®.
1Experian 2024 Data Breach Industry Forecast
2Statista.com – 2020: Annual number of data breaches and exposed records in the United States from 2005 to 2020
4Child monitoring includes up to 5 children under the age of 18. One-time Parent/Legal Guardian verification is required to receive alert details for children.
5Calculated on the VantageScore 3.0 model. Your VantageScore 3.0 from Experian® indicates your credit risk level and is not used by all lenders, so don’t be surprised if your lender uses a score that’s different from your VantageScore 3.0. Click here to learn more.